New open-source IVPN website: subscribe without providing your email
IVPN News By Viktor Vecsei | Posted on November 10, 2020
In a nutshell
Generating an account for our VPN service no longer requires an email address, and we dropped renewing subscriptions by default in favor of a pre-paid system. We have introduced a new onboarding process with QR code setup, and two-factor authentication for account IDs that act as a sole identifier.
We have also changed our website structure and copy, emphasizing our policies and the limitations of VPNs. The website is now open-source on GitHub and supports light/dark mode switching.
Why the changes?
We’ve been vocal about the shortcomings of the VPN industry and our competitors for multiple reasons. Two of them stand out:
- VPN services promise privacy protection, yet most of them collect and share personally identifiable information about you. Methods for this include using Google Analytics, website trackers and third-party tools - all shunned by IVPN. A handful of services stopped these violations, but yet they still require an email address to sign up. Disclosing your email address makes you personally identifiable and should not be necessary to subscribe to a privacy protection service.
- Most VPN services over-promise on the actual value they offer - they claim to make you anonymous and invisible on the internet and pledge to solve every privacy problem online. As we have demonstrated in a previous blog post, false promises are rampant on VPN websites, marketing materials and landing pages. We aim to do better, and do it in the most transparent way possible.
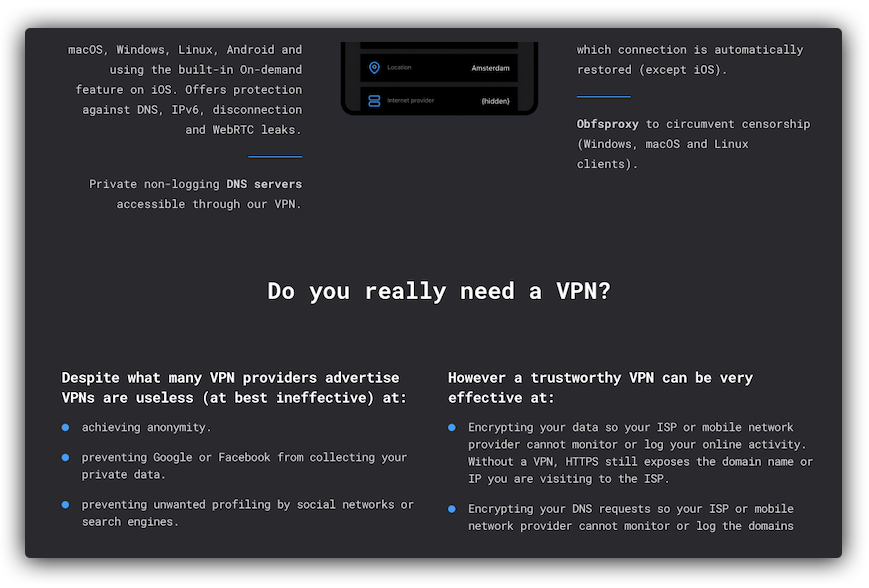
What has changed exactly?
- We have dropped the email address requirement and removed our initial signup form. From now on, customers create a unique identifier instantly by pressing a ‘Generate account’ button. The generated Account ID is the only information you need to manage your account and use our service (please keep it secret, keep it safe - 2FA is supported). If you pay for your subscription with cash or anonymously sourced cryptocurrency, no personally identifiable information can be tied to your IVPN account.
- Our subscriptions are now pre-paid by default. Getting a recurring subscription is optional during account generation, and we don’t store any payment details unless you ask us to. You can now add 2 and 3 years of service time with one payment (and a discount).
- We have revamped our website and written new copy that’s clear on VPN capabilities and their value for privacy protection. Review our home page to see how we think a responsible VPN service should communicate without overselling or creating fear, uncertainty, and doubt.
- The IVPN website - following precedent set by our apps - is now open-source. Source code is available on GitHub. You can follow changes to any page on ivpn.net, e.g. our Privacy Policy or Terms of Service.
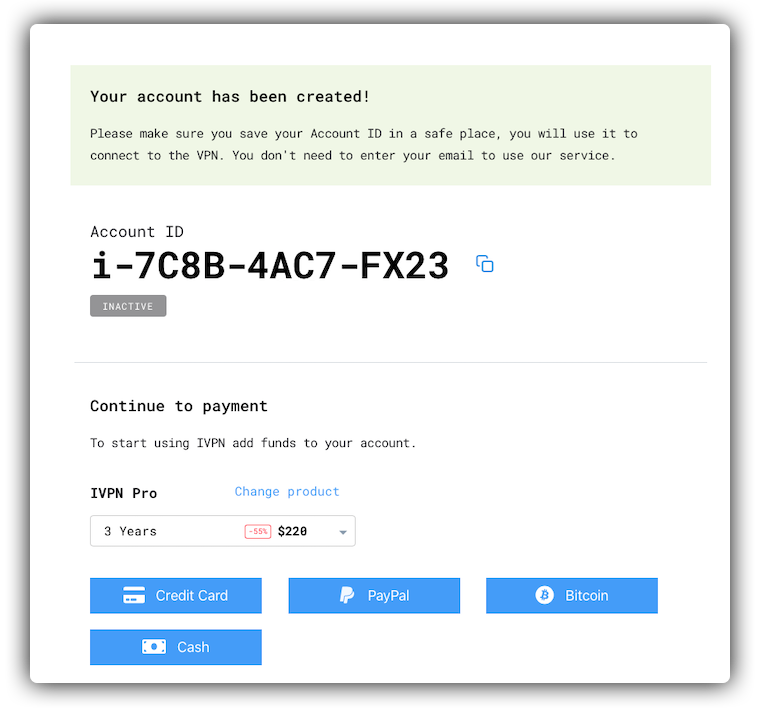
Note to current IVPN subscribers:
- As a first step, we have implemented our new account creation flow and client area only for newly created subscriptions.
- We plan to migrate each existing, previously created account to the new system later this year and offer an automated method for removing your email address on file.
IVPN Staff
Suggest an edit on GitHub.
