Heartbleed – What passwords to change
Privacy & Security By Ed Holden | Posted on April 10, 2014
**Graphic updated on **16/04 @ 17:37 CEST - (Netflix changes)
The Heartbleed bug - a major security flaw in OpenSSL - has seriously disrupted the online community this week. OpenSSL is one of the most popular pieces of encryption software, and the bug has potentially exposed millions of user details to hackers.
Some online service providers acted quickly, patching the flaw as soon as it was announced. However, many others have yet to act.
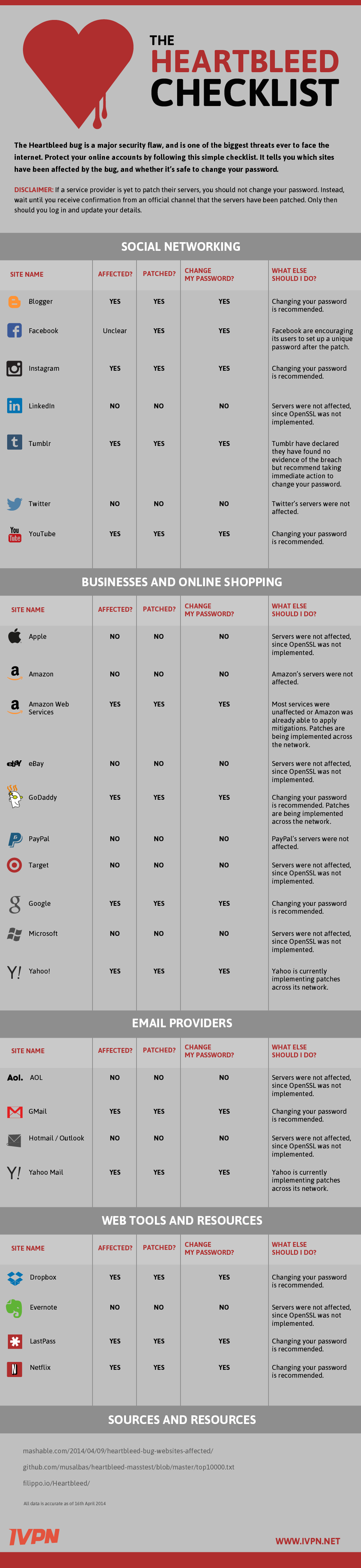
If a service provider is yet to apply the patch, you should not change your password. Instead, wait until you receive confirmation from an official channel that the servers have been patched. Only then should you log in and update your details.
Conflicting reports have led to panic - nobody seems to know which sites have been affected, or whether their servers have been patched.
To dispel the confusion, we’ve created a simple password change checklist. It identifies the major sites which have been affected by Heartbleed - and whether they’ve patched their servers yet.
Suggest an edit on GitHub.


4 Comments
James Bryce
12.04.2014
Rich
12.04.2014
Barry Rueger
13.04.2014
If a service provider is yet to apply the patch, you should not change your password. Instead, wait until you receive confirmation from an official channel that the servers have been patched.
I probably have log in IDs at at least 50 to 75 web sites here and there. To date not one of them has e-mailed me to say “Hey we fixed it, now change your password.”
This advice is pretty much useless unless system admins are pro-active in letting users know when systems have been patched.
David
13.04.2014
I seriously question the advice that passwords not be changed until the site has announced that it has applied the fix. This simply leaves the user vulnerable if in fact their password is compromised.
I think better advice is to identify those sites where compromise would have a serious impact … e.g., a bank or investment account … and change those passwords frequently … e.g., daily … until AFTER the fix is applied … be sure to make one last change AFTER the fix.
Of particular concern would be any email providers for accounts which could be used to recover password access to other accounts.